![]()
Krypton is a privacy tool that uses strong encryption to securely protect personal and confidential information resident on your iOS (and macOS) devices. Krypton is not a password manager: it encrypts and decrypts entire folders and documents (text, spreadsheets, images, audio and video, recipes, emails, anything).
Topics
Metaphorically, Krypton keeps your ciphertext items in a special vault, with each item contained in its own deposit box — to gain access to a ciphertext item the vault must be open, and to gain access to its plaintext contents the passcode key must be used to unlock the deposit box. For iOS the vault may be open or closed, while on macOS the vault opens upon Log In.
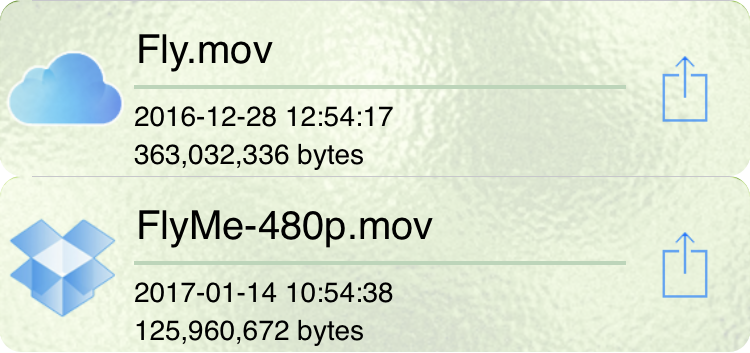
When the vault is open previously encrypted ciphertext items are displayed in alphabetical order, each represented by its name, creation date, size and one of these icons:
The icon describes the location of the ciphertext: a vault ciphertext document resides locally on your iOS or macOS device; an iCloud Drive or Dropbox ciphertext document resides on the cloud and must be downloaded to the vault before it can be decrypted.
Touching a vault ciphertext item performs the default action upon that item:
For iOS the vault is open by default — Settings is where you enable Vault Security and its open and close mechanisms. With the vault closed and secured, prying eyes cannot even see the
names of your ciphertext items. With vault security enabled, when entering the background Krypton closes the vault automatically.
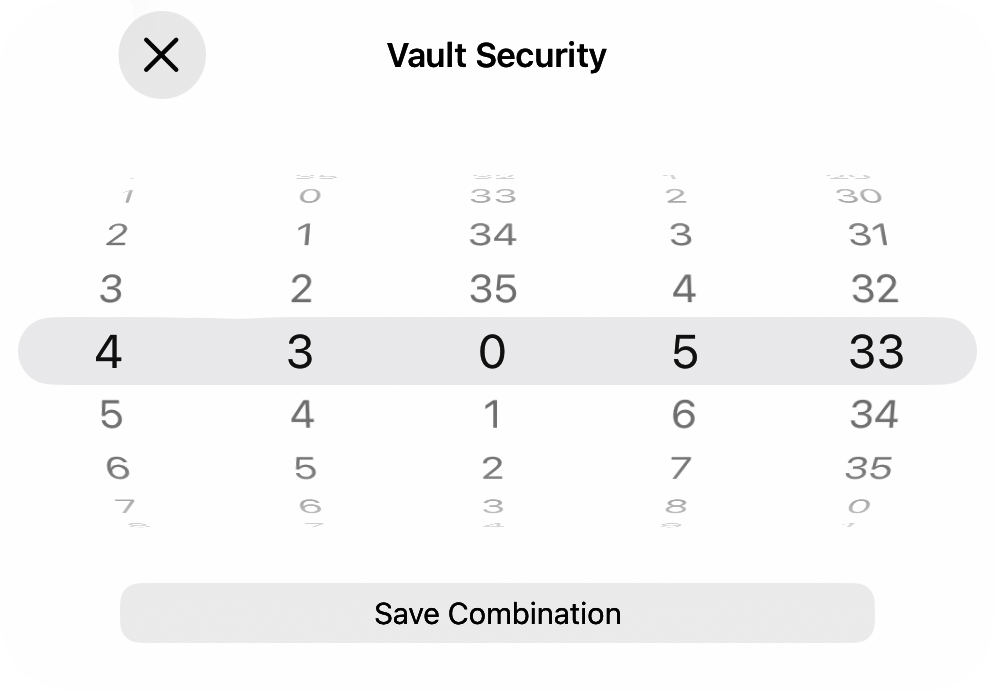
Vault security is activated with a 5-number combination that is entered using a number picker:
This combination is also used to remove vault security — please do not forget it.
Various mechanisms open Krypton's vault door:
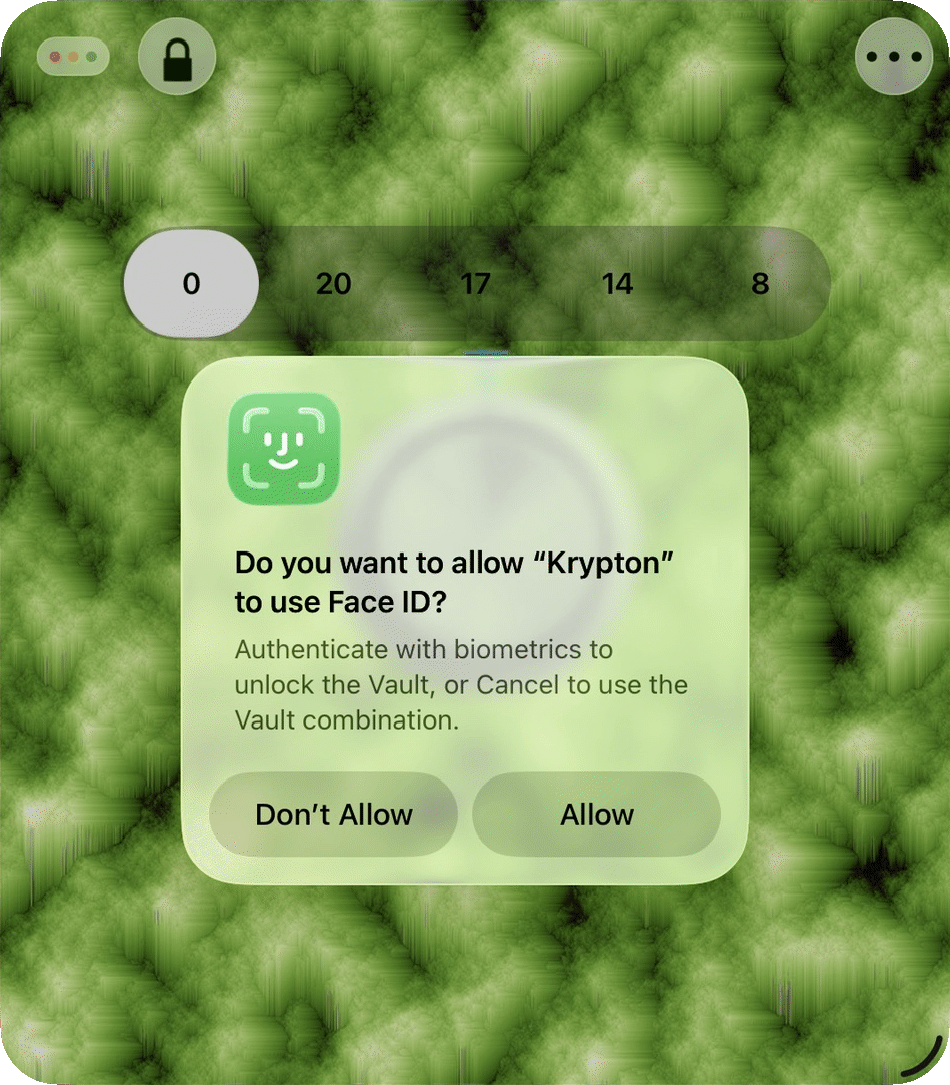
The first time you encounter a closed vault door you could see this:
Enable biometrics if so inclined, then the vault opens without having to enter the combination — otherwise you're presented with an unlock control used to enter the combination. After entering the combination touch the door open/close padlock button at the top-left.
When using the twistable knob, select each of the 5 number segments in turn and dial its combination number, then press the unlock button.
Here are the two unlock controls, shown in their Dark Appearance.
The top-right button (whose icon may be an ellipsis or keyboard) discloses other ways to open the vault, depending upon device and iOS version.
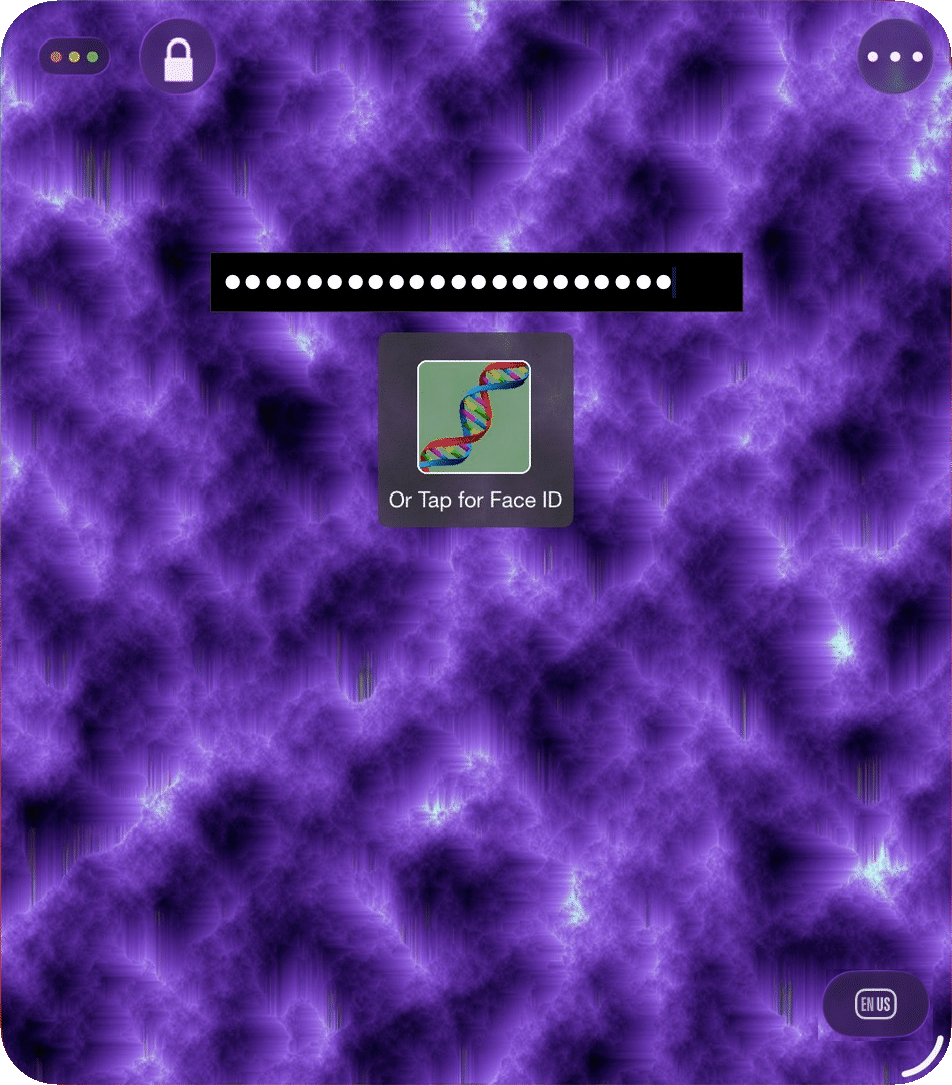
When opening the vault via the keyboard enter your 5-number combination in the text field,
separating each number by one or more non-digit characters (use more non-digit characters for obfuscation if someone is watching).
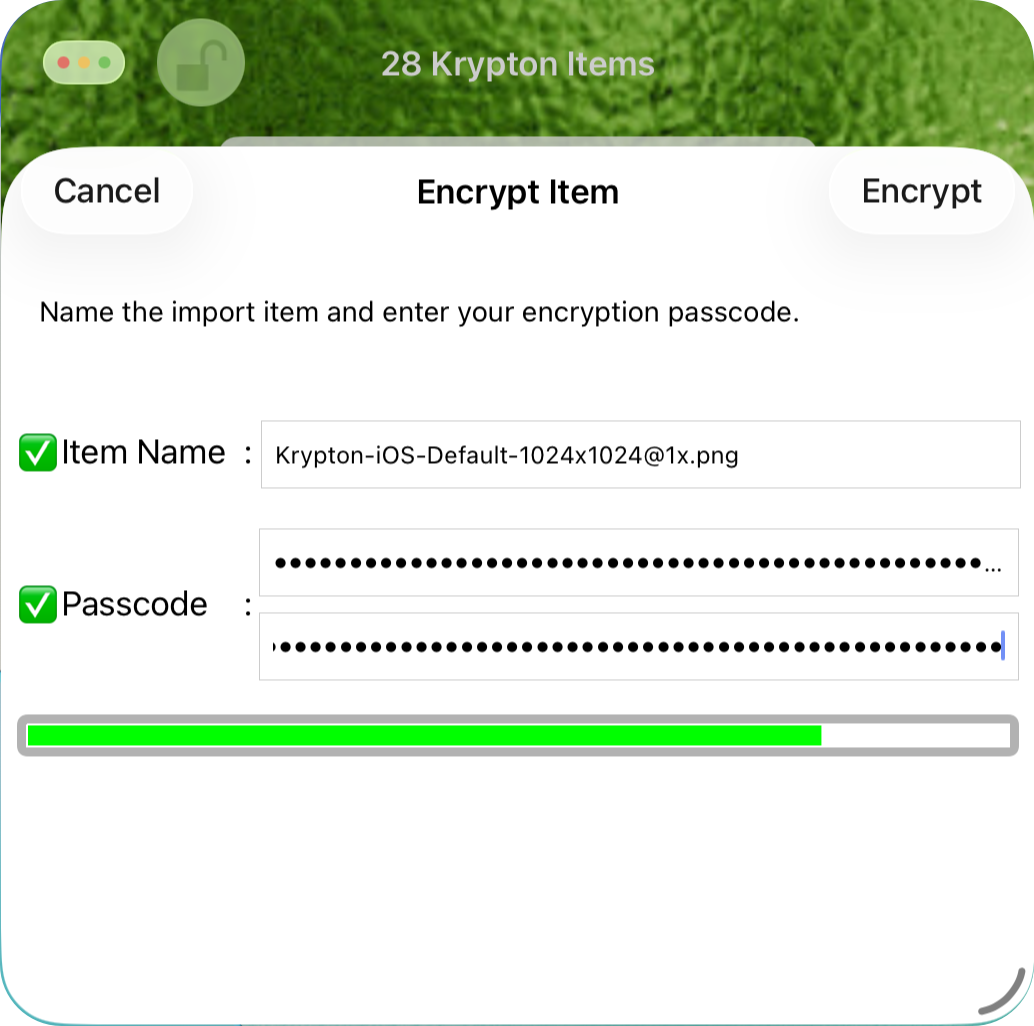
You can import items into Krypton's vault using Files, AirDrop, File Sharing, other Apps, or from iCloud Drive or Dropbox. If the imported item is plaintext it's first encrypted and then stored in the vault; already encrypted items are simply copied to the vault, they are not re-encrypted.
Pasteboard Copy & Paste is the primary information import mechanism, via the innocuous button shown below — if you've performed an interesting Copy the button could change to:
The pasteboard is erased after any encryption attempt, successful or unsuccessful.
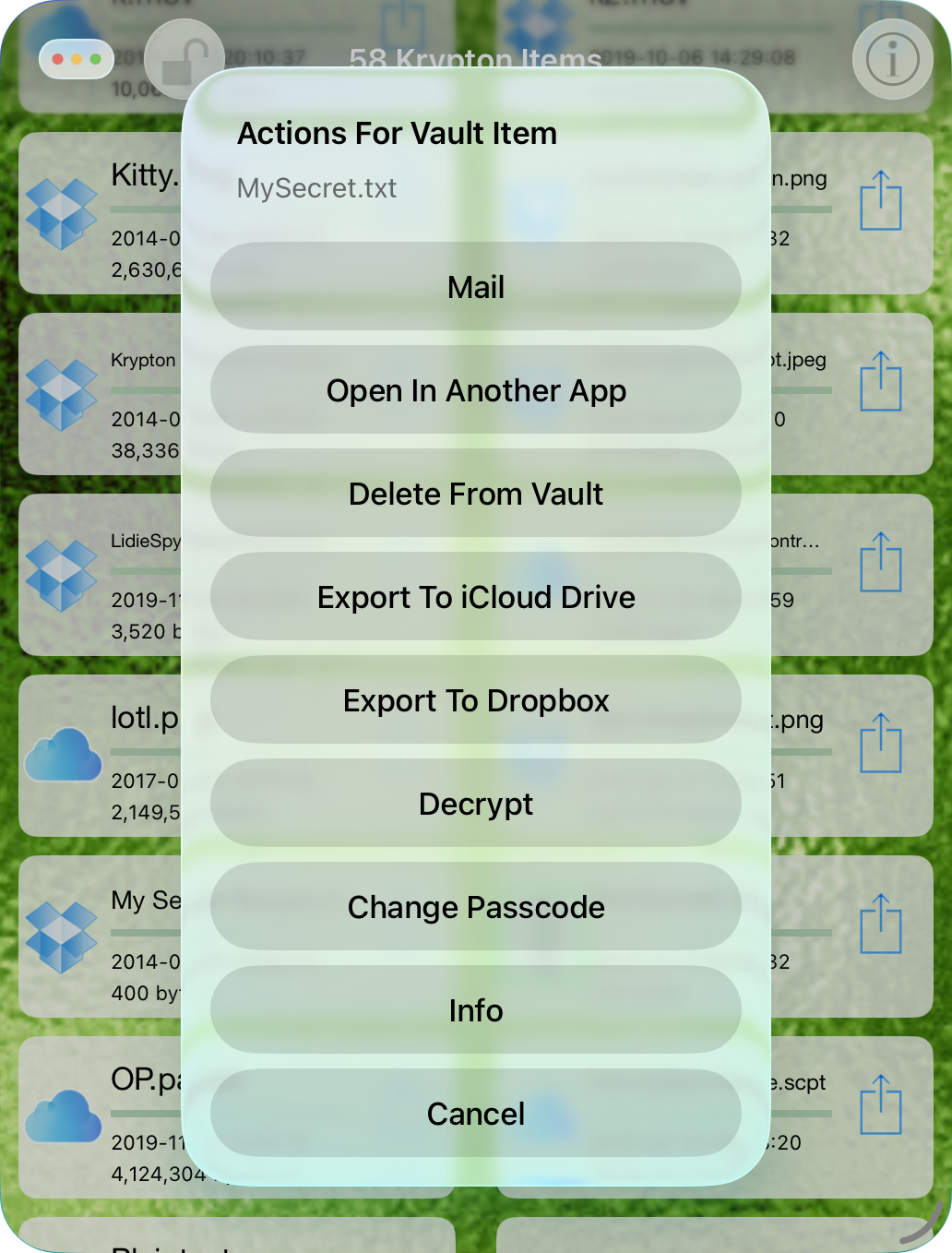
Touch a vault item's Action button to see possible actions, which vary depending on the item's state. For example:
Mail transmits a copy of the ciphertext outside the vault. Open In Another App transfers a copy of the item to another App.
Delete From ... removes the item from the vault or iCloud Drive or Dropbox.
Plaintext is shredded, while ciphertext is deleted.
Deleting an iCloud Drive or Dropbox item removes the ciphertext from your device, iCloud Drive or Dropbox and all synchronized computers and mobile devices. Import From ... copies the ciphertext to the vault from iCloud Drive or Dropbox. Export To ... copies the ciphertext from the vault to iCloud Drive or Dropbox. Change Passcode changes the passcode for ciphertext items created by Krypton for macOS version 3, or iOS version 4, and higher. A dialog asks for the item's current and new passcodes. Krypton uses the current passcode to first authenticate the ciphertext, and assuming that is succesful, the passcode change operation commences — for a 1.5 GB file this will take approximately 5 seconds on an iPhone 17 Pro.
Because your encrypted file is randomly re-written in-place, you must NOT interrupt the change process. Do not leave Krypton, do not lock your screen or power-off your Macintosh. Doing so will almost certainly lead to irrecoverable data loss.
After a change passcode action successfully completes, cloud-based Krypton items are automatically pushed up to iCloud Drive or Dropbox.
After decryption Krypton
tries to display the plaintext in a Viewport. Common file formats are supported, such as text, images, Office
and iWork documents, HTML, and so on.
Simple text files — any file with a .txt or .html extension, or that iOS
recognizes as Unicode strings — are displayed with long lines wrapped in the Viewport. To prevent wrapping, open the Viewport by double-tapping the ciphertext item, the plaintext may be horizontally scrolled.
In Krypton's world, plaintext data is meant to be ephermeral and fleeting, to exist for as little time as possible,
and then to be shredded. You may choose to shred the plaintext data you are examining as soon as you leave the Viewport, or you may choose to keep it
around temporarily. If you elect to keep the plaintext when exiting the Viewport and returning to the vault, the item's icon changes to a red alert triangle:
Temporarily retaining the plaintext may be a good choice for items that decrypt slowly and that you plan to revisit several times while in the vault.
However, plaintext data
is always shredded when Krypton terminates or enters the background, unless you disable this feature, selectable in Settings.
The shredder runs as a background thread, dutifully destroying plaintext data, either yours or intermediate temporary files. When the
shredder is active you'll see this chomper in the vault's title bar:
Shredding is an expensive and important operation that runs at high priority and pre-empts other tasks — be patient when it's active.
When Krypton shreds an item it first overwrites the file with a pattern of all ones, followed by a second pass of all zeros, before deleting the file. Any files that escape shredding at App termination, for whatever reason, are shredded the next time Krypton runs.
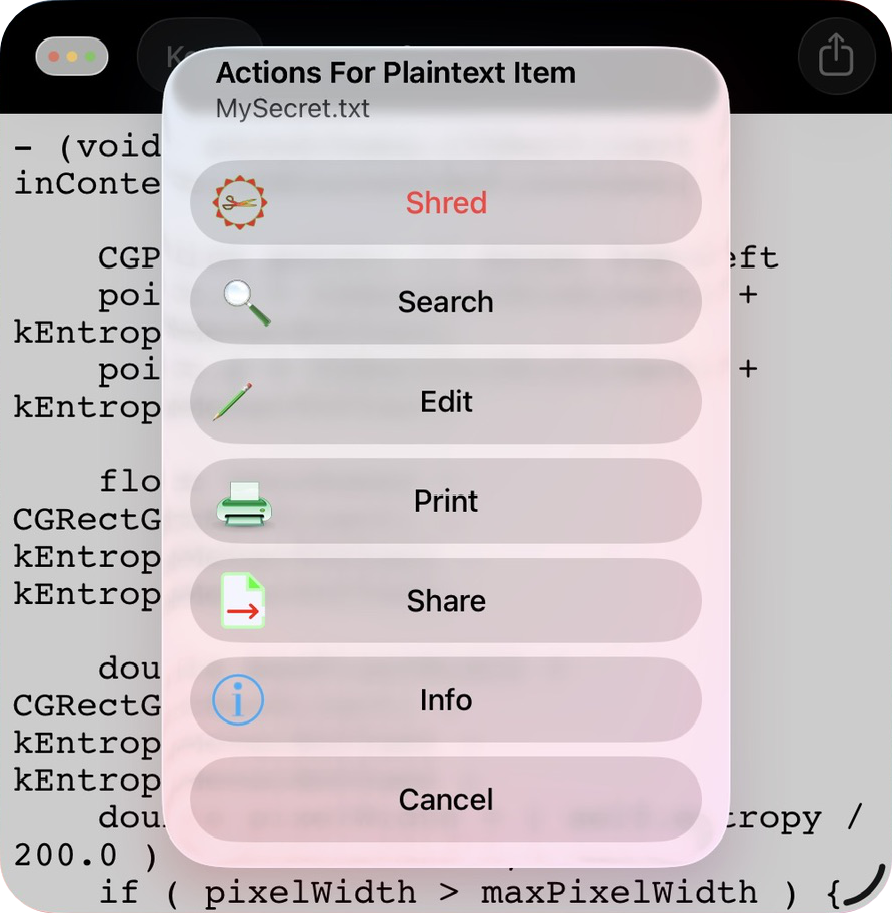
Touch the plaintext item's Action button to see possible actions, which vary depending on the item's state. For example:
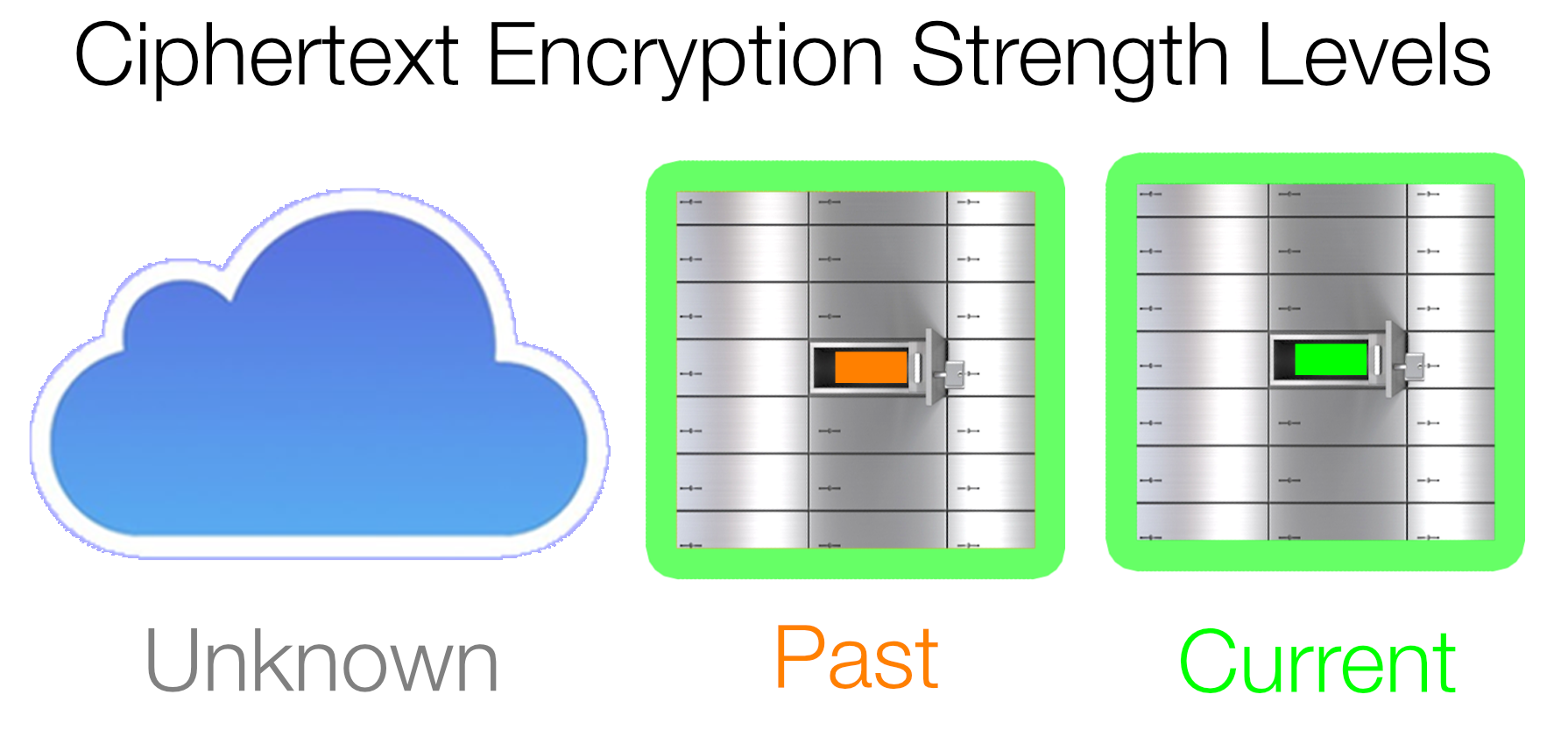
Crypto best practices are constantly evolving, and occassionally Krypton's cipher (encryption algorithm) is strengthened accordingly. Once Krypton has incorporated another cipher all newly encrypted documents are generated in this format, such that, over time, your collection of encrypted documents may encompass several ciphers.
Krypton distinguishes these ciphers using a small LED in the ciphertext item's deposit box. For vault items that are in the cloud and not resident on the device the LED is unlit and not visible. Otherwise the LED is lit, and for vault items with the current cipher the light glows green — for vault items encrypted with older ciphers the LED glows orange. Although Krypton will continue to decrypt all past and current ciphers, it is in your best interest to re-encrypt older plaintext with the latest cipher.
iCloud Drive support is controlled by iOS in Settings / Apple ID / iCloud Drive. Dropbox support is controlled by Krypton in Info / Settings.
Krypton documents on iCloud Drive (or Dropbox) must first be imported before they can be decrypted and viewed. After touching Action and selecting Import From iCloud Drive (or Import From Dropbox)
the item is marked busy until the download completes and the ciphertext is stored in the vault. At that point you use the item as you normally would. If you swipe to
delete the vault copy of an iCloud Drive-backed (or Dropbox-backed) document only the vault item is removed. But if you swipe to delete the iCloud Drive (or Dropbox) item then the ciphertext is
removed from your device, iCloud Drive (or Dropbox) and all synchronized devices.
To move an item from the vault to iCloud Drive (or Dropbox) touch Action and select Export To iCloud Drive (or Export To Dropbox).
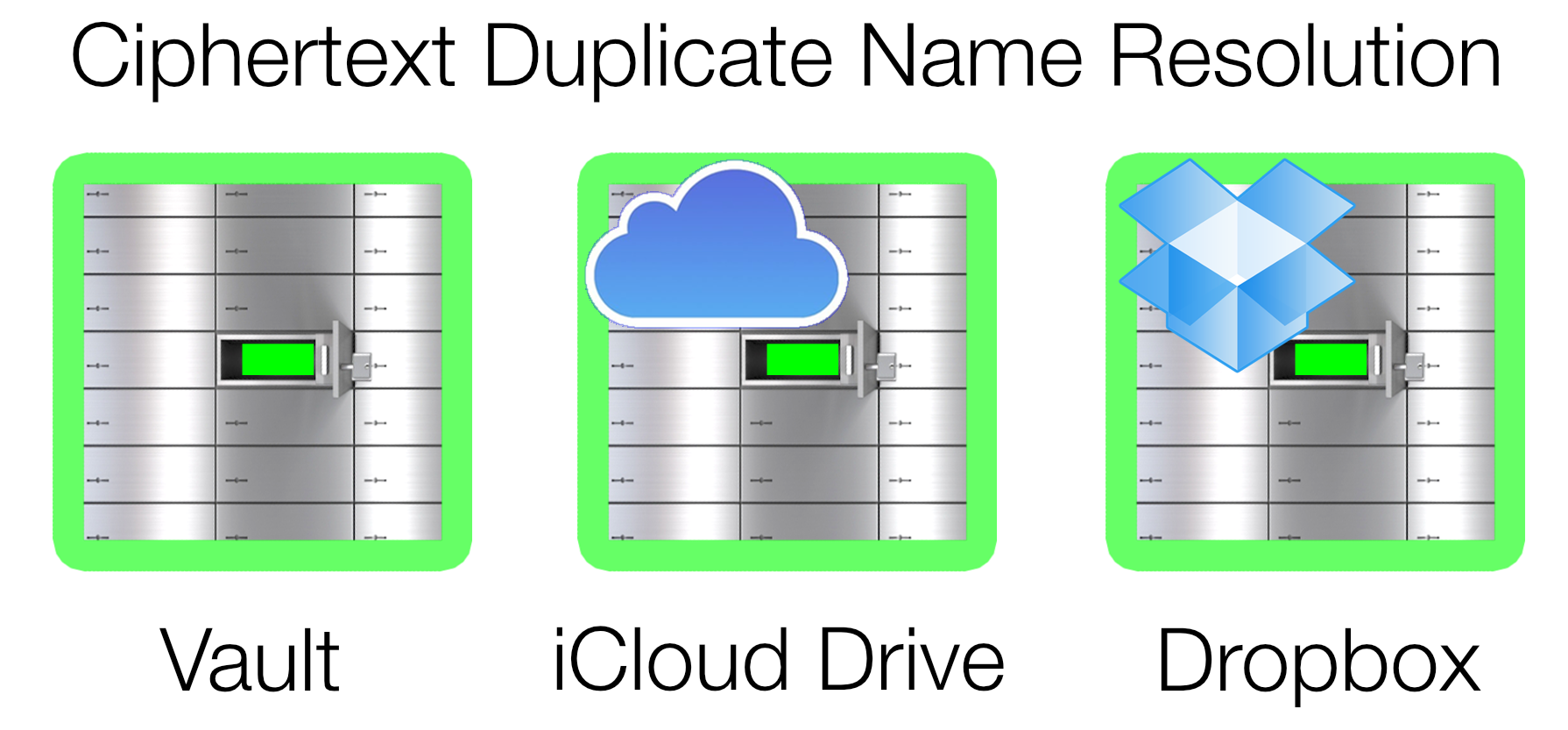
Krypton handles iCloud Drive (and Dropbox) version conflicts simply: the last document pushed to iCloud Drive (or Dropbox) wins. So, if you create encrypted
documents having identical names on two offline devices, then as each device goes online it stores its version of the document on iCloud Drive (or Dropbox); consequently, the
second copy overwrites the first and becomes the true copy.
Krypton distinguishes vault items that have duplicate names by displaying a tiny overlay indicating the item's cloud repository source.
Terminology
The Vault

Opening and Closing the Vault

Import Plaintext and Ciphertext
Vault Actions
The Plaintext Viewport

The Shredder
Plaintext Viewport Actions
Ciphers
iCloud Drive and Dropbox Documents
Gesture Summary
What's New?
iOS 14.0 - 26.2
iPadOS 14.0 - 26.2
macOS 11.0 - 26.2
visionOS 1.0 - 26.2
26.2 - 2026.01.02
- Bug fixes and improvements.
- Info action enhanced.
- Refreshed documentation.
- Update for DropBox SDK 7.4.1
- Update for Apple OS versions 26.2.
8.2.1 - 2022.10.11
- iOS 16 security changes to Mobile Safari broke the display of some types of plaintext.
- Minimum iOS version is 11.0.
- Update for iOS 16.0.2.
8.2 - 2022.02.25
- Minor bug fixes and improvements.
- Update for iOS 15.3.1, macOS 12.2.1.
8.1 - 2021.02.13
- Krypton now uses short-lived Dropbox tokens, which means you will have to re-authenticate occasionally.
- New macOS Universal binary that runs on either Apple Silicon or Intel Macs.
- Update for iOS 14.4, macOS 11.2.
8.0 - 2020.09.19
- Krypton is now a single purchase that runs on your iPod touch, iPhone, iPad and Macintosh.
- Update for iOS 13.6.1.
7.2 - 2020.06.09
- Conform with Apple's 2020.06.30 App Store guidelines.
- Update for iOS 13.5.1.
7.1 - 2019.11.16
- After a change passcode action successfully completes, cloud-based Krypton items are automatically pushed up to iCloud Drive (or Dropbox).
- Improve the Viewport display (enhance the algorithm that differentiates a folder from an application).
- Document folder encryption.
- Update for iOS 13.2.3.
7.0 - 2019.11.07
- Add ability to import and encrypt folders.
- When the Encrypt button reads Check For Pasteboard Data touching it evaluates the pasteboard contents for importable items.
- Update documentation with Import examples, particularly Open In usage for iWork documents and the Files App.
- Krypton is now Dark Mode aware.
- Krypton works in full screen, split view and slide view.
- Bug fixes. All deprecated APIs updated as well.
- Update for Dropbox 3.10.0.
- Update for iOS 13.2.2.
6.9 - 2019.03.22
- Update for iOS 12.1.4.
- Documentation now supports BigCatOs Appearances.
6.8 - 2018.09.14
- Update for iOS 12.0.
- Documentation updates.
6.7 - 2018.01.10
- Update for iOS 11.2.2.
- Improve Sharing with other Apps.
- Clarify Face ID's effect on importing and encrypting from the pasteboard.
6.6 - 2017.11.21
- Update for iOS 11.1.2 and iPhone X.
- If Vault Security is enabled your options for unlocking the Vault now include the combination control, the keyboard, and, if enabled, Touch ID or Face ID.
- Improve background thread handling.
- Bug fixes.
6.5 - 2017.10.26
- Update for iOS 11.0.3.
- Full support for iPhone X.
- Improve background thread handling.
6.4 - 2017.07.23
- Documentation updates.
- Update for iOS 10.3.3.
6.3 - 2017.05.25
- Rewrite Dropbox code for new API version 2.
- iOS version 9 or greater now required.
- Update for iOS 10.3.2.
- Bug fixes.
6.2 - 2017.01.22
- Refresh various images; documentation tweaks.
- Bug fixes.
6.1 - 2017.01.04
- Fix Open In of a Zip file.
- Update and consolidate plaintext and Zip Viewport display code; fix clipped text when pencil-editing.
- Use AlertController framework to modernize and consolidate alert and action dialogs.
- Remove the Viewport toolbar of actions and replace with a popup menu of possible actions. The Actions menu is activated via the Action button that replaces the Keep button on the right of the Viewport. The Keep button is now on the left of the Viewport where Shred used to be, and Shred is now an item in the Actions menu.
6.0 - 2016.12.21
- Update for iOS 10.2.
- Critical performance (not data integrity) bug fix for iPhone and iPod.
- Various, smaller, bug fixes.
- Krypton now requires that your iDevice run an iOS version >= 8.
5.0
- Re-add iCloud Drive support.
- Use Touch ID to unlock the Vault.
- iPhone 6 and iPhone 6 Plus aware.
- Update for iOS 8.1.
4.2
- Update for iOS 8.
4.1
- For files encrypted with Krypton for iOS version 4 (or Mac OS/X version 3) and higher, add the ability to change the ciphtertext passcode without having to re-encrypt the file.
- Share and Import have been combined into Action, which includes the Change Passcode feature.
- You can now paste a long and complex passcode via the pasteboard into the encryption and change passcode dialog views. (You must first disable Shred Plaintext in Settings.)
- When importing a Dropbox document into the vault, the item's creation date inherits the Dropbox file creation date.
- You can pencil-edit a plaintext text file once again.
4.0
- Completely re-written to take advantage of features in iOS 6 and later.
- New, more secure encryption format that authenticates your ciphertext via Encrypt-Then-MAC. Thanks to Jeffrey Goldberg of 1Password for his technical writings on the subject.
- Encryption / decryption uses less memory and is approximately 14% faster. To put this in perspective, an iPhone 5S is almost as fast as a current generation iMac!
- Maximum document size increased to 4 GB for 64-bit iOS devices (2 GB for older devices).
- New iPad user interface displays Vault items in a matrix rather than a single column.
- Vault items can be sorted alphabetically either up or down, or re-ordered manually by touching for 1 second and dragging.
- Pull down to poll data sources such as macOS File Sharing and Dropbox to refresh the Vault's contents.
- Like iPad, every iPhone and iPod view can now be rotated.
- Dynamic Type that adjusts most text to your preferred reading size.
- Auto Layout so Krypton is ready for all those rumored larger iDevices!
- Update for iOS 7.1, 64-bit clean.
3.0
- Update for iOS 7.
- Similar to plaintext, ciphertext items are now protected by the device's hardware encryption keys.
2.11
- Add pasteboard support for encrypting a QuickTime movie directly from the Camera roll.
2.10
- One bug fix, but it was a doozy!
2.9
- iOS 6 tested.
- Improved iTunes File Sharing.
- Support for new iPhone and iPod larger screen size.
- With Vault Security enabled, randomize the combination and auto-lock the vault when entering the background.
2.8
- Bug fixes only this time.
2.7
- Add button to refresh Dropbox document list.
- Add ability to download and encrypt Dropbox plaintext documents.
2.6
- Add Dropbox support in lieu of iCloud, using the folder /Apps/Krypton as your ciphertext vault in the cloud.
- More Advanced Kryptonology: ability to export decrypted Zip folders that you manually created.
2.5.1
- Remove support for iCloud documents, per Apple's request. Please refer to the FAQ How do I recover Krypton documents stranded on iCloud? for more information.
2.5
- Do not backup plaintext to iCloud.
- For iPad display plaintext fullscreen rather than in a popover.
2.4
- iCloud document support.
2.3
- Large document support.
- Robust shredder, with activity view.
- Improved memory management and subtle bug fixes.
Copyright (©) 2009 - 2026 BigCatOS. All rights reserved. | Contact